The SimJacker vulnerability, uncovered by AdaptiveMobile Security, exploits a common SIM card flaw to affect nearly a billion Android, iOS, eSIM and IoT devices.

Also Read :- Facebook may start hiding 'Like' counts from posts
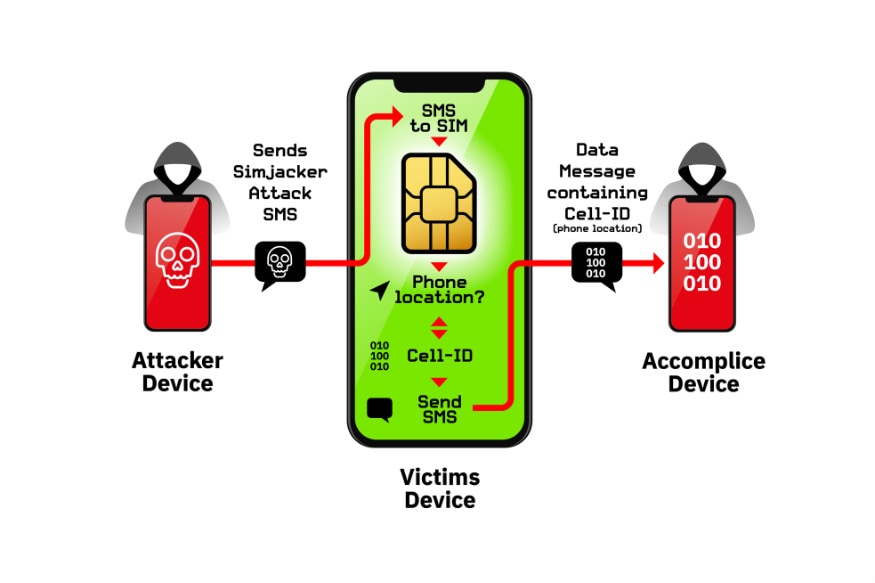
SimJacker, a new vulnerability discovered by researchers, has been linked to a widely used software that affects SIM cards used commonly across 30 countries. In what appears to be a critical threat, the flaw is reportedly exploited by simply sending a text message to target devices, which in turn activates specific SIM card instructions that can be used to spy on active location of individuals, send fake messages on behalf of the device owner, make fraudulent calls, force-install malware, steal critical information and more such serious acts.
The flaw has been discovered by AdaptiveMobile Security, a frontline provider of real-time cyber-telecom security technologies. While reports indicate that the proof of concept of the attack is yet to be submitted, AdaptiveMobile CEO Cathal McDaid says, "We are quite confident that this exploit has been developed by a specific private company that works with governments to monitor individuals.
As well as producing this spyware, this same company also have extensive access to the SS7 and Diameter core network (both critical network backbone infrastructure), as we have seen some of the same Simjacker victims being targeted using attacks over the SS7 network as well, with SS7 attack methods being used as a fall-back method when Simjacker attacks do not succeed."
To execute such attacks, the infiltrator is only required to send a message that resembles a system code message that is actually a malware code that directly communicates with the SIMalliance Toolbox Browser (or S@T Browser).
This is a piece of software that is present in a wide volume of SIM cards across many nations in the world. In a blog post detailing the vulnerability, AdaptiveMobile states that S@T Browser is a legacy protocol, whose technology specifications have not been upgraded in over a decade now. However, by virtue of it being present in SIM cards, attackers are making use of its ability to take actions such as send system messages, set up an operator call, launch specific browser links and send requisite data to a target address.
As a result, sensitive data such as live location, device IMEI number and more are being collected in what appears to be a silent espionage project. McDald says, "By using these commands in our own tests, we were able to make targeted handsets open up web browsers, ring other phones, send text messages and so on.
These attacks could be used to fulfil such purposes as mis-information by sending SMS/MMS messages with attacker controlled content, fraud by dialling premium rate numbers, espionage as a location retrieving attack, espionage as a listening device by ringing a number, malware spreading by forcing a browser to open a web page with malware located on it, denial of service by disabling the SIM card, information retrieval such as language, radio type, battery level etc. — it even may be possible to go even further, depending on handset type."
What is particularly more alarming is that unlike Check Point's recently uncovered vulnerability that arose due to a flaw in the over-the-air update system message being sent on Samsung, Huawei, LG and some other Android devices, the SimJacker vulnerability does not require any action to be taken by a mobile phone user.
Also Read :- Humans were built to remember only important things. The internet is disturbing that balance
Instead, it works completely in the background, thereby working as a deadly surveillance tool for any agency with such intentions. The SimJacker vulnerability is also device agnostic, and works with the same intensity across devices made by OEMs such as Apple, Samsung, Google and Huawei — all leaders in the smartphone space. The threat is also imminent on IoT devices, which employ certain builds of eSIM, hence further expanding its potential to what AdaptiveMobile refers as "over a billion individuals across the world".
McDald states that AdaptiveMobile has already been in touch with telecom operators in the affected nations, and are working with them to issue a fix. This fix in question would come from an operator's end, which can block fraudulent system messages that carry such malware and spyware-ridden code.
The company has also communicated the same to GSM Association and SIMalliance, and will be revealing more details about the SimJacker flaw at the Virus Bulletin Conference in London, on October 3.
You have provided a nice article, Thank you very much for this one. And I hope this will be useful for many people. And I am waiting for your next post keep on updating these kinds of knowledgeable things. esim india
ReplyDelete